Concepts and Terminologies
This page provides explanations and links to concepts and terminologies used in the Identity Manager to help users better understand the service.
Identities
An identity is a personal data record that may include biometric information for identification, a face photo, a unique external user ID, and other metadata information. It is the primary type of resource managed in the Identity Manager service. The service instance level manages identities and cannot be shared among different instances.
Identities are essential in using facial recognition solution services. Most of the solution services require the existence of an Identity Manager service instance within the same service region. Updating Identity Manager identities will be automatically reflected in solution services.
An identity requires an external user ID as its primary key. A user ID can be the employee ID of your organization or the consumer ID of your service. This key should be unique inside the service instance and cannot be updated once the identity is created. If you want to change that ID, please insert a new identity with the updated user ID and then delete the old one.
Groups
An identity group is a collection entity to include multiple identities for management and application purposes. There is no hierarchical relationship between groups and identities. That is to say, deleting one of the resources would only remove the mapping but not delete the related resources. An identity can belong to multiple groups, and a group can contain multiple identities, offering flexibility in identity management.
There are no limits on the following items.
- The number of groups the user can create.
- The number of identities can be added to one group (limited by the identity numbers allowed by the plan).
- The number of identities can be added to / removed from a group in one batch operation.
A group can be made from various perspectives. Common ones include teams, locations, ranks, and time of entry. The group is not required but can be very helpful in some solution services based on the Identity manager.
Template
An identity template is a customizable identity data structure. Each Identity Managerinstance can have up to one template that applies to all identities.
The template feature acts as two roles.
- Expand the available data fields for identity storage.
- Validate all new data inputs to encourage the use of structured data.
One template can have up to 20 custom fields that users configure. Each field includes several attributes to be configured before it can be used. For more details on the custom field setting, please refer to the Template section. Custom fields are managed by their unique IDs internally instead of by their names, making updating their attributes after creation possible without impacting the data stored. Deleting a custom field will also delete all values of this field attached to identities. So be cautious with the deletion.
All custom fields are displayed in the Other information area on the single identity operation pages. The template setting works as a validation checker before reaching the identity database by checking the input field type and value every time the user adds or updates an identity. Please notice that the validation check only applies to new entries or updates but will not trace back existing data. As a result, some identity data fields may not obey the rules set for some custom fields as they are old entries, as long as they are not updated. The settings are also applied to OpenAPI endpoints when creating or updating a single identity, except for the Nullable setting. This is due to the limitation of data parsing in the backend service. The Nullable setting is only applicable on the GUI pages.
Identity Provisioning
Identity Provisioning is a process of automatically keeping identity resources consistent between different identity providers. As the modern business evolves, enterprises are now using multiple systems for their HR, training, sales, and office systems, all based on the same employee base. There is a need to have a single identity source across these various systems to reduce the cost of maintenance and delay. Common practice is to use the email provider system as the identity source, such as Microsoft or Google, and synchronize necessary information to other systems.
As for JCV Cloud, the system is designed for digital and physical access control based on biometric recognition technologies. Like other applications acting as the receiver side of identity provisioning, Identity Manager also provides an Azure AD provisioning solution based on SCIM.
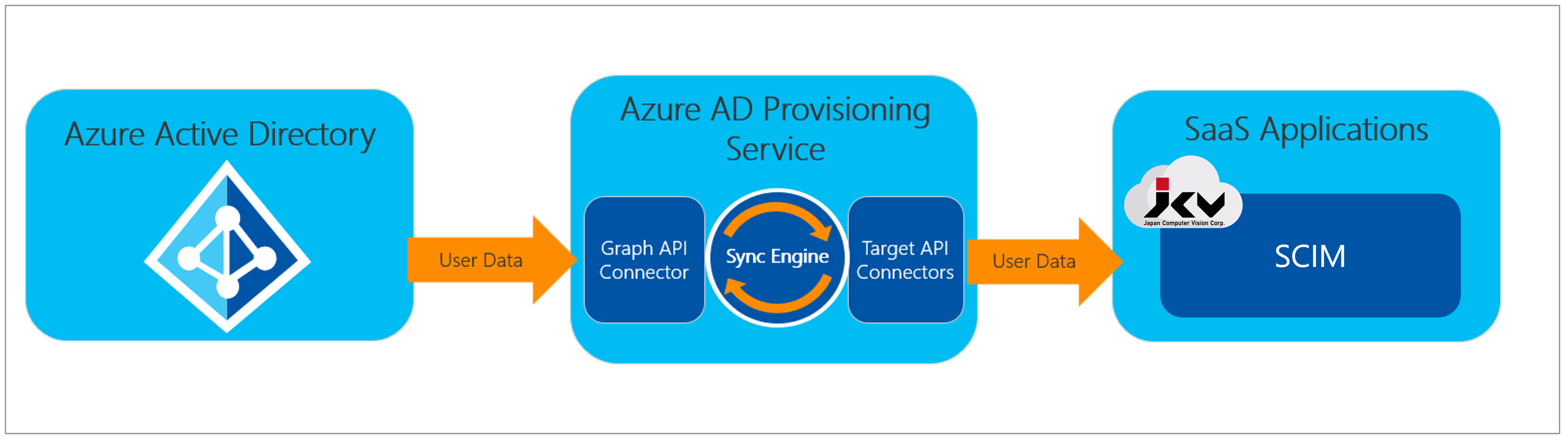
Identity Provisioning by SCIM
By setting up the SCIM server and provisioning settings correctly, any changes (adding, deleting, and updating) of identities on Azure AD will be reflected in Identity Manager by the frequency set by the users. Please refer to this section for more details.
Updated 9 months ago
